Vumetric Your trusted penetration testing provider
Selecting the right penetration testing provider is a critical decision for any organization looking to strengthen its cybersecurity posture. This process involves evaluating various factors to ensure that the provider you choose is capable of identifying vulnerabilities and securing your network effectively. But what exactly should you consider in making this decision? Let’s explore the key criteria and questions to ask when choosing a penetration testing provider.
- Outsourced provider or in-house testing: which is better?
- What expertise and experience are necessary for a provider?
- What certifications should specialists have?
- Which methodologies & standard are employed?
- What to expect from a professional report?
- How can you assess penetration testing process?
What's a Penetration Test?
Penetration testing involves simulating cyber attacks to identify vulnerabilities in a business’s IT systems. It’s crucial for enhancing security by exposing weaknesses before malicious attackers can exploit them. This proactive measure helps businesses strengthen their defenses, safeguard sensitive data, and comply with regulatory requirements, thereby protecting their reputation and financial stability.
Benefits of a Provider vs In house Testing team
Choosing between engaging a specialized penetration testing provider and developing an in-house testing team is a pivotal decision for organizations aiming to enhance their cybersecurity posture.
Expertise
Providers offer specialized knowledge and experience, ensuring comprehensive testing.
Cost-Effective
Outsourcing can be more economical than maintaining an in-house team.
Objectivity
External providers offer unbiased assessments, free from internal influences.
Advanced Tools
They have access to the latest testing technologies and methodologies.
Compliance
Providers ensure testing meets industry standards and regulatory requirements.
Time-Saving
Allows your internal team to focus on core business tasks.
Network Penetration Testing Services
Focuses on identifying security risks in both internal and external network configurations, including firewalls and VPNs.
- External Network Penetration Testing
This testing focuses on identifying vulnerabilities from an outsider’s perspective, ensuring IT infrastructures and applications are guarded against evolving external threats and hacking methods. - Internal Network Penetration Testing
It aims to uncover vulnerabilities within the organization’s network that automated tools might miss, simulating potential insider attacks or breaches that have surpassed external defenses. - Wireless Network Penetration Testing
With increasing compliance standards, this testing assesses wireless network security against unauthorized access, ensuring these networks do not become gateways for cyber threats. - Mainframe Penetration Testing
Targets the security of mainframe systems, identifying gaps that standard security measures like firewalls and antivirus might not cover, ensuring comprehensive protection. - Industrial SCADA Penetration Testing
Specialized testing for Industrial Control and SCADA systems, focusing on vulnerabilities unique to networks controlling physical processes, crucial for maintaining operational integrity in industrial sectors.


Application Penetration Testing Services
Assesses web, mobile applications, and APIs against common vulnerabilities, incorporating manual tests to uncover complex issues.
- Web application penetration testing
This involves deep dives into web applications using manual tests to reveal complex vulnerabilities, offering a detailed security assessment beyond what automated scans can detect. - Mobile Application Penetration testing
Simulates hacking techniques to uncover vulnerabilities in mobile apps, focusing on areas like unauthorized access and software exploitation, identifying key security weaknesses. - API Penetration Testing
Assesses APIs against recognized security standards to determine their external security posture, helping gauge their resilience to common vulnerabilities. - Thick Client Penetration Testing
Targets desktop applications with advanced security measures to mitigate a broad spectrum of threats, aiming to minimize potential attack vectors. - Source Code Review
A meticulous examination of an application’s source code to spot security flaws early, integral for reinforcing security from the initial development stages.
Cloud Penetration Testing Services
Evaluates security in cloud-hosted assets across major platforms like AWS, Azure, and Google Cloud, considering unique cloud configurations.
- Amazon Web Services (AWS) Penetration Testing
Analyzes AWS environments, including network configurations, firewalls, IDS/IPS, and VPNs, to identify and mitigate potential security issues. - Microsoft Azure Penetration Testing
Assesses Azure-hosted web and mobile applications and APIs against common vulnerabilities like the OWASP top 10 and business logic flaws. - Microsoft Office 365 Security Audit
Reviews security across cloud platforms (AWS, Azure, Google Cloud), examining specific components and configurations for vulnerabilities. - Google Cloud Platform Penetration Testing
Tests the security of devices and applications within Google Cloud, covering medical devices, consumer products, and IoT devices, focusing on their features and protocols.

Adversary Simulation / Red Team
Simulates real-world cyberattack scenarios to test the effectiveness of an organization’s security measures, including employee response to phishing attempts.
- Red Team Assessment
Performs a thorough external penetration test that goes beyond standard automated scans, providing a detailed security evaluation of the organization’s external network defenses. - Purple Team Assessment
Mimics hacking tactics and exploits, like unauthorized access and software vulnerabilities, to identify and strengthen the organization’s most susceptible points. - Phishing Simulation Test
Conducts targeted phishing campaigns to test employee awareness and response, serving as a practical measure of the organization’s security awareness training effectiveness.
Compliance
To align with various compliance standards and regulations, Vumetric’s penetration testing services focus on identifying and rectifying security vulnerabilities that could jeopardize compliance
PCI DSS
Ensures payment systems are secure and vulnerabilities that could expose cardholder data are addressed.

SOC 2
Verifies the security of services provided by SaaS companies, focusing on the protection of customer data.

GDPR
Identifies potential security gaps that could lead to breaches of personal data, emphasizing data protection.

FDA
Ensures that medical devices comply with cybersecurity standards to protect patient data.

ISO 27001
Helps establish, implement, maintain, and continuously improve an information security management system (ISMS).
Discover Why Organizations Choose Vumetric
Vumetric is a boutique company entirely dedicated to providing comprehensive penetration testing and specialized cybersecurity services. We pride ourselves on delivering consistent and high-quality services, backed by our ISO 9001 certified processes and industry standards. Our world-class cybersecurity assessment services have earned the trust of clients of all sizes, including Fortune 1000 companies, SMBs, and government organizations.
Specialized Expertise
Certified Professionals
Proven Methodologies
Independance & Impartiality
Reputation & Trust
No Outsourcing
Cybersecurity Solutions by Industry
Finance & Insurance
Comply with standards and secure sensitive data.
Manufacturing
Secure smart production lines and equipment.
Healthcare
Secure medical devices and protect patient care.
Education
Protect teacher and student data.
E-Commerce
Secure online payments and customer data.
SaaS & Technology
Secure critical assets and meet requirements.
Transport
Secure your smart supply chain and fleets.
Startups
Learn about our Startup discount program.
Government
Secure public services and sensitive data.
Energy & Utilities
Secure energy production and distribution systems.
Certified Team of Security Experts
Partner with the best in the industry to protect your mission critical IT assets against cyber threats.














Our Penetration Testing Process
Here’s a high-level overview of each stage in our proven penetration testing process. We keep you informed at every step of the project.
Project Scoping
Duration: ~ 1-2 days
Activities: We learn about your specific needs and objectives.
Outcome: Business proposal, signed contract.
Kick-off / Planning
Duration: ~ 1 hour
Activities: We review the scope of work, discuss requirements and planning.
Outcome: Scope validation, test planning.
Penetration Testing
Duration: ~ 2-3 weeks
Activities: We execute the test in accordance with the project scope.
Outcome: Detailed penetration test report, presentation.
Remediation Testing
Duration: Up to 1 month
Activities: We test and validate vulnerability fixes.
Outcome: Remediation report, attestation.
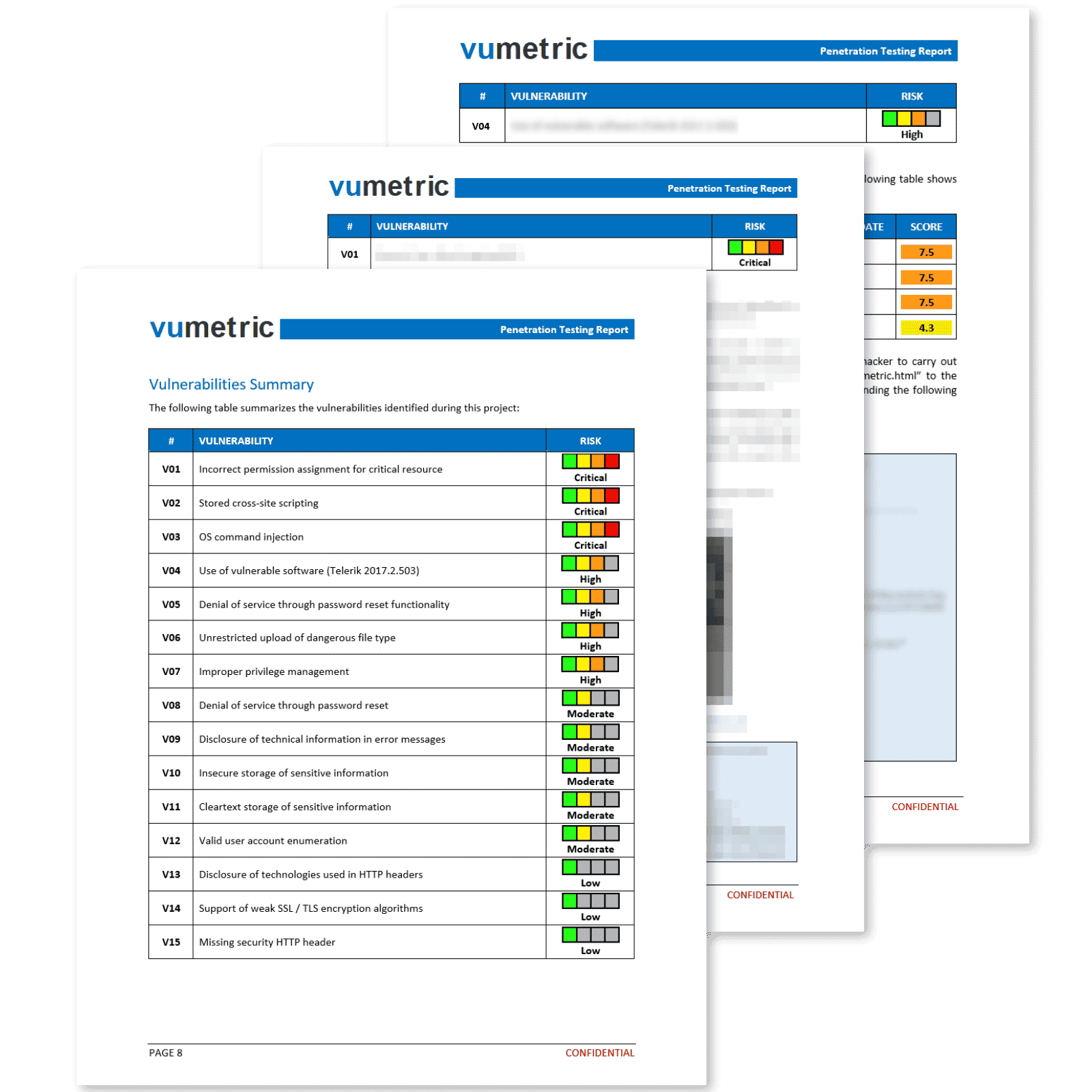
Professional Reporting With Clear & Actionable Results
Our penetration reports deliver more than a simple export from a security tool. Each vulnerability is exploited, measured and documented by an experienced specialist to ensure you fully understand its business impact.
Each element of the report provides concise and relevant information that contributes significantly towards improving your security posture and meeting compliance requirements:
Executive Summary
High level overview of your security posture, recommendations and risk management implications in a clear non-technical language.
Suited for non-technical stakeholders.
Vulnerabilities & Recommendations
Vulnerabilities prioritized by risk level, including technical evidence (screenshots,
requests, etc.) and recommendations to fix each vulnerability.
Suited for your technical team.
Attestation
This document will allow you to meet compliance and regulatory reporting requirements efficiently and with minimal overhead.
Suited for third-parties (clients, auditors, etc).
Vumetric PTaaS Platform
Vumetric’s Penetration Testing as-a-Service (PTaaS) platform is designed for organizations looking for a modern solution to manage their cybersecurity assessments.
- Request new cybersecurity projects on-demand
- View & compare previous results all in one place
- Track the real-time progress of your assessments
- Invite your team members & manage their permissions
- Available on AWS & Azure Marketplaces
Penetration Testing Guide
(2024 Edition)
Everything you need to know to scope, plan and execute successful pentest projects aligned with your risk management strategies and business objectives.
- The different types of penetration tests and how they compare
- The use cases of vulnerability scans VS. pentests
- The industry's average cost for a typical project
- What to expect from a professional report
- 20 key questions to ask your prospective provider
External Penetration Testing
Case Study
See our industry-leading services in action and discover how they can help secure your external network perimeter from modern cyber threats and exploits.
- Project findings of a real external pentest project
- List of identified vulnerabilities prioritized by risk level
- Attack path overview and steps
- Outcome of the project
- And more
Web Application Penetration Testing
Case Study
See our industry-leading services in action and discover how they can help secure your mission-critical Web Apps / APIs from modern cyber threats and exploits.
- Project findings of a real external pentest project
- List of identified vulnerabilities prioritized by risk level
- Attack path overview and steps
- Outcome of the project
- And more
Internal Penetration Testing
Case Study
See our industry-leading services in action and discover how they can help secure your internal network infrastructure from modern cyber threats and unauthorized access.
- Project findings of a real internal pentest project
- List of identified vulnerabilities prioritized by risk level
- Attack path overview and steps
- Outcome of the project
- And more
Penetration Testing Methodologies

Open Web Application Security Project
An organization offering resources to improve software security, known for the OWASP Top 10 list of web application security risks.

MITRE ATT&CK FRAMEWORK
A knowledge base detailing real-world adversary tactics and techniques, used for developing threat models and methodologies.

Open Source Security Testing Methodology
A framework for security testing that ensures thorough, consistent, and repeatable assessments, focusing on penetration testing and vulnerability analysis.

NIST SP 800-115
Guidelines from NIST for securing web services, offering best practices for their development, deployment, and maintenance.

Penetration Testing Execution Standard
A standard for penetration testing that provides a common framework and language for conducting security tests.

The Information Systems Security Assessment Framework
A framework for assessing the security of information systems, covering everything from planning to reporting.
Cybersecurity Standards

CVE
Common Vulnerabilities and Exposures

CVSS
Common Vulnerability Scoring System

CPE
Common Platform Enumeration

OVAL
Open Vulnerability and Assessment Language

CAPEC
Common Attack Pattern Enumeration and Classification

CWE
Common Weakness Enumeration

CWSS
Common Weakness Scoring System

NVD
National Vulnerability Database
Read Our Clients' Success Stories
Discover how our pentest services helped organization of all kinds improve their network security:
“ Vumetric conducted penetration testing and showed us where we were vulnerable. They made the process smooth, were very responsive and well organized. They really impressed us as specialists in their field. ”
Elizabeth W., General Manager
" Vumetric provided penetration testing services and delivered comprehensive results in a timely manner. They dedicated a highly-skilled, knowledgeable team with excellent customer service. ”
Joe A., IT Infrastrucure Manager
“ Vumetric performed manual and automated security testing of our systems. They met our deadlines and kept us updated throughout the testing process. Their presentation of findings and recommendations was engaging and effective. ”
Louis E., Director of IT & CISO
Penetration Testing FAQ
Couldn’t find the information you were looking for? Ask an expert directly.
Penetration tests, in spite of their necessity, are still a simulation of a cyberattack on your systems and applications. Depending on how rigorous or experienced your provider is, penetration tests can cause numerous inconveniences for your team and service disruptions for your customers. You want to work with a company that understands the potential hazards, has the necessary measures in place to mitigate any testing impacts, and will work with you to ensure that no down times or inconveniences occur during the test. You may also want to take this opportunity to advise your penetration tester about any sensitive areas that could disrupt your business. An experienced pentester is expected to identify and safely exploit vulnerabilities within your system without causing any harm or denial of services
When you work with a penetration testing company, you want to know who you’re working with. It is highly recommended to look for a company that does the work themselves, rather than outsourcing it to contractors. Over the course of the test, the specialists in charge may stumble upon highly sensitive data or identify vulnerabilities that could have a severe impact on your business. When projects are outsourced, many challenges arise when it comes to confidentiality and accountability. Trusted providers and experienced companies vetting their candidates require a thorough background check for each of their testers; they also use various measures to ensure the confidentiality of your data, the consistency of their deliverables, and the documentation of each step taken by the specialist.
Finding vulnerabilities is only one portion of what you’re looking to accomplish with a penetration test. When you’re hiring a plumber, you’re expecting more than a report explaining how your pipes are clogged. For pentesting, you should hire a company that not only presents their findings and lists actionable recommendations with external references, but also provides post-test support to help your team fix these vulnerabilities. This includes re-testing any critical/high-severity vulnerabilities to validate the implementation of the recommended corrective measures. As you’re looking for a penetration tester, be sure to ask how they will help fix your vulnerabilities.
Tell us About your Needs Get an Answer the Same Business Day
What happens next:
A Vumetric expert will contact you to learn more about your cybersecurity needs and goals.
The project's scope will be defined (Target environment, deadlines, requirements, etc.)
A detailed quote including all-inclusive pricing and statement of work is sent to you.






