COMPREHENSIVE & EXPERT-DRIVEN
PENETRATION TESTING SERVICES
Our hands-on approach combines the latest techniques used by hackers, as well as top industry standards in order to uncover any vulnerabilities that would be exploited in a real-world attempt to breach your cybersecurity and propose adapted counter-measures.
- Identify vulnerabilities beyond the capabilities of an automated penetration test
- Get detailed step-by-step recommendations on how to fix them
- Achieve compliance with standards (SOC 2, PCI-DSS, ISO 27001, etc.)
- Inform management on risks and remediations
- Gain full confidence in your cybersecurity
Get In Touch With Our Team
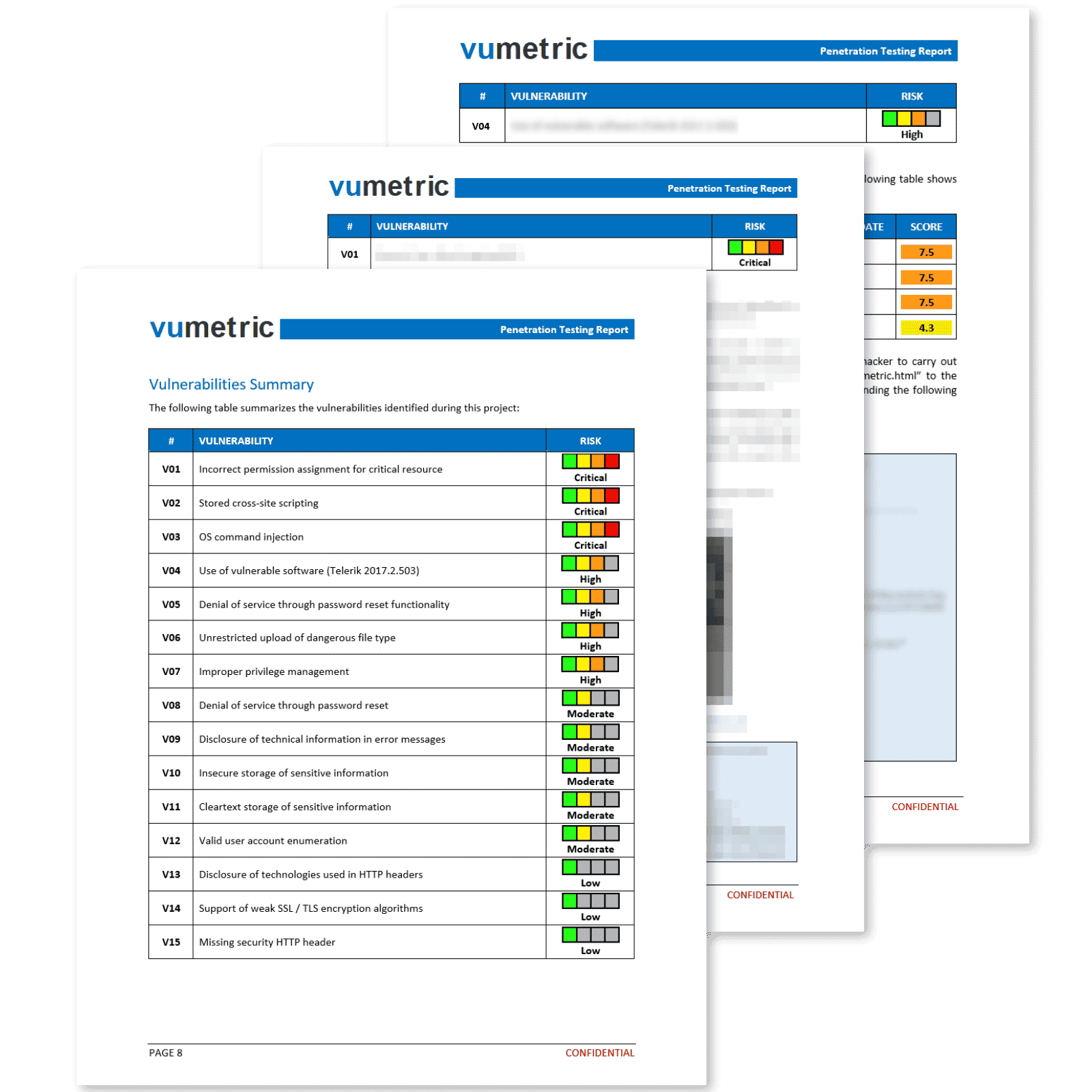
Professional Reporting With Clear & Actionable Results
Our penetration testing reports deliver more than a simple export from a security tool. Each vulnerability is exploited, measured and documented by an experienced specialist to ensure you fully understand its business impact.
Each element of the report provides concise and relevant information that contributes significantly towards fixing your vulnerabilities, improving your security posture and meeting compliance requirements:
Executive Summary
High level overview of your security posture, recommendations and risk management implications in a clear, non-technical language.
Suited for non-technical stakeholders.
Vulnerabilities & Recommendations
Vulnerabilities prioritized by risk level, including technical evidence (screenshots,
requests, etc.) and recommendations to fix each vulnerability.
Suited for your technical team.
Attestation
This document will allow you to meet compliance and regulatory reporting requirements efficiently and with minimal overhead.
Suited for third-parties (clients, auditors, etc).
Industry Leaders Count on Vumetric to Improve Their Cybersecurity
“ They had friendly staff and realistic down-to-earth recommendations ”
Mark D, IT Director
Mid-Market
“ I'm impressed by the common sense and technical skills of the team. ”
Carl P, Director of Infrastructure & Security
Mid-Market
“ The team is extremely knowledgeable in what they do ”
Wes S, IT Manager
Enterprise
“ Amazing team of experienced cybersecurity professionals! ”
VP, Research and Development
Mid-Market
Explore the latest customer reviews for Vumetric’s penetration testing and cybersecurity solutions to dive deeper into how we help organizations of all types.




Download Our External Penetration Testing Case Study
See our external penetration testing services in action and discover how they can help secure your public-facing network perimeter from modern cyber threats and exploits.
Download Our Medical Device Penetration Testing Case Study
See our medical device penetration testing services in action and discover how they can help secure your smart healthcare equipment and its underlying components from modern threats to achieve FDA compliance.
Download The Vumetric Penetration Testing Buyer's Guide
Learn everything you need to know about penetration testing to conduct successful pentesting projects and make informed decisions in your upcoming cybersecurity assessments.
Download Our Web Application Penetration Testing Case Study
See our Web App penetration testing services in action and discover how they can help secure your mission-critical applications and APIs from modern cyber threats and exploits.
Download Our Internal Penetration Testing Case Study
See our internal penetration testing services in action and discover how they can help secure your internal network infrastructure from modern cyber threats and unauthorized access.
Certified Penetration Testing Team
Our experts hold the most widely recognized penetration testing certifications. Partner with the best in the industry to protect your organization against the latest cyber threats.










Why Organizations Trust Vumetric's Penetration Testing Expertise
Top methodologies
Our testing methodologies are based on known best practices and key technological standards in the industry (OSSTMM, OWASP, NIST, CVE, CVSS, STIX, CAPEC, etc).
Impartiality
Unlike many competitors, we do not resell hardware or software solutions. This ensures that our recommendations are focused on your organization’s real cybersecurity needs.
Experienced team
Our consultants have extensive
real-world experience and hold the most recognized certifications in the industry (OSCP, OSWE, GWAPT, GPEN, OSEP, CISA, CCSE, CCSA, CISM, CISSP, etc.)
No outsourcing
All our projects are executed internally by our team of highly-vetted specialists to ensure the consistency of the quality of our deliverables and the confidentiality of your information.
We Help You Streamline Compliance
We can help your organization achieve compliance with various cybersecurity standards efficiently and with minimal overhead.
- ISO/IEC 27001 Information Security Management
- SOC 2 Type I & Type II
- PCI-DSS for the Payment Card Industry
- HIPAA For Health Care
- GDPR General Data Protection Regulation
Proven Methodologies & Standards
We are committed to delivering the highest quality and most consistent services using world-class methodologies and standards (OWASP, OSSTMM, MITRE ATT&CK, etc.)
- OWASP for Application Security
- MITRE ATT&CK Framework
- OSSTMM Open Source Security Testing Methodology
- PTES Penetration Testing Execution Standard
The Limitations of Automated Testing
Limited scope
Automated testing can only detect known vulnerabilities in a predefined set of systems and applications. In contrast, manual penetration testing can adapt to different environments and identify vulnerabilities in proprietary applications with unique configurations.
Lack of context
Automated tools do not understand the context of an organization’s environment or the potential impact of a vulnerability. Expert-driven penetration testing provides a better understanding of the risks, prioritizing them based on the organization’s specific needs.
Limited modern exploits
Automated tools may struggle to keep up with the latest attack techniques used by cybercriminals, as they rely on predefined exploits. Manual pentesting leverages human ingenuity and creativity, as well as knowledge of the current threat landscape to identify & exploit vulnerabilities that automated tools consistently miss.
Limited capabilities
Automated tools can have difficulty exploiting complex vulnerabilities that require a multi-step process or chaining of different weaknesses. Expert-driven penetration testing can uncover these sophisticated attack paths that lead to significant breaches.
Limited remediation guidance
Automated tools often provide generic remediation advice that may not be applicable to a specific organization’s environment. Manual penetration testing offers tailored recommendations, considering the unique context of the risk in the organization.
False positives / negatives
Automated tools may generate false positives, flagging issues that are not actual vulnerabilities, or false negatives, missing real security risks. Expert-driven penetration testing validates findings to ensure you focus remediation efforts on the right priorities.

Real-Life Example of a Hacker's Attack Path

Penetration Testing Services Tailored To Your Needs
Application
Penetration Testing
Identify business logic and technical vulnerabilities in mobile applications, web applications, websites & APIs.
Learn More →
Medical Device
Penetration Testing
Fix vulnerabilities in your medical equipment to protect patients and meet FDA requirements.
Learn More →
Network Security
Penetration Testing
Identify security gaps in external networks and secure internal servers from unauthorized access.
Learn More →
Penetration Testing For Compliance Requirements
Meet the compliance requirements of various security standards (PCI-DSS, SOC 2, ISO 27001, NIST, etc.)
Learn More →
Cloud Infrastructure Penetration Testing
Secure cloud-hosted assets and environments (AWS, Microsoft Azure, Google Cloud, etc.)
Learn More →
SCADA / ICS
Penetration Testing
Secure smart production lines and industrial equipment from disruptive attacks. (Production, logistics, ICS, etc.)
Learn More →
What Happens After You Reach Out?
We communicate at every step of the project to keep you informed.
We Discuss Your Needs
After submitting the form, a specialist contacts you within 24 hours to review your objectives and discuss a potential project. We provide more details regarding estimated pricing and our testing process
You Receive a Proposal
Within 2 to 3 business days, you receive a no-engagement proposal with the all-inclusive pricing for your penetration testing project, including more details on our testing methodologies.
We Schedule a Kick-off Call
Following your approval, a call is scheduled to review the testing scope, determine a point of contact for critical vulnerability escalations and to set a launch date.
Penetration Test & Retesting
The assessment is performed by our team and results in a detailed report with all findings and recommendations. The outcome is presented to your stakeholders.

FAQ About Penetration Testing
Couldn’t find the information you were looking for? Ask an expert directly.
What is the purpose of conducting a penetration test?
The process involves an initial pre-engagement phase to define scope and objectives, followed by reconnaissance, scanning, exploitation, and post-exploitation stages to identify vulnerabilities and assess potential impacts. Detailed reports are provided after testing to help you understand and address discovered issues.
How is it conducted? What is the process?
Web application pen test should ideally be performed at least annually to ensure consistent security against evolving threats. Additionally, it’s recommended to conduct a pen test after any significant changes or updates to the application or its hosting infrastructure, as new features, integrations or modifications can introduce new unknown vulnerabilities.
How much does it cost?
The cost of a penetration test varies significantly according to a number of factors. The most determining factor is the size (such as the number of the IP addresses being targeted) and the complexity of the testing scope (the number of features in an application, for instance).
Learn more about the main factors that determine the cost of a penetration test →
Quickly receive a free quote with no engagement using our streamlined quoting tool →
Can penetration testing cause disruptions or downtimes?
Our penetration tests are designed to minimize disruption to your organization’s normal operations and the overwhelming majority of our tests are unnoticeable to our clients. Our team will work with you prior to the project launch to determine any areas that may be susceptible to affect your productivity and will take the necessary steps to minimize any potential impact.
Do we need to provide any access or permissions for the test to be conducted?
In most cases, no access or permissions are required for a penetration test. The goal is to replicate an authentic cyber threat attempting to circumvent your security measures therefore the test is conducted entirely without any inside knowledge or access. However, some types of tests may require access is required to achieve the desired outcome. For example, in order to accurately test an industrial system, remote access to the network may be needed. We will coordinate with your team during the project launch call, where we will confirm objectives, the testing target, as well as any access requirements to achieve project goals.
Will the test allow us to meet compliance requirements?
Our penetration tests helps several organizations of all types meet compliance requirements every year by identifying vulnerabilities that need remediation. Once remediation testing is completed, we provide an official attestation confirming that vulnerabilities have been remediated, helping organizations meet compliance requirements efficiently without requiring them to share confidential and sensitive information regarding their cybersecurity risks to a third-party.
How long does it take?
The duration of the test varies depending on the size and complexity of the scope. A typical pentest project can range from a few days, up to 3 weeks.
Additional Penetration Testing Resources
Got an Upcoming Project? Need Pricing For Your Penetration Test?
Answer a few questions regarding your cybersecurity needs and objectives to quickly receive a tailored quote. No engagement.
- You can also call us directly: 1-877-805-7475