AWS Cloud Infrastructure Security Audit
Explore the security of your rapidly expanding AWS infrastructure with Vumetric’s comprehensive audit. Stay ahead of evolving digital threats and ensure your cloud environment is robustly secured.
What you'll get:
- Vulnerability Insights: In-depth report on AWS security gaps.
- Risk Overview: Executive summary of risk implications.
- Benchmark Alignment: Strategic compliance with CIS standards.
- Mitigation Plans: Tailored AWS security strategies.
- Q&A Debrief: Detailed report walkthrough with clarity session.
What is this Service?:
AWS penetration testing by Vumetric is a specialized assessment aimed at identifying and addressing vulnerabilities within Amazon AWS Cloud infrastructures. While Amazon provides secure tools for cloud configuration, maintaining the stability and security of your environment remains your responsibility. Our service offers proactive measures to address potential breaches and helps you understand the security implications of changes in your AWS setup. Thus, AWS penetration testing becomes an essential tool for ensuring the stability and security of your Amazon AWS environment, aligning with the rapid digital transformation across industries.
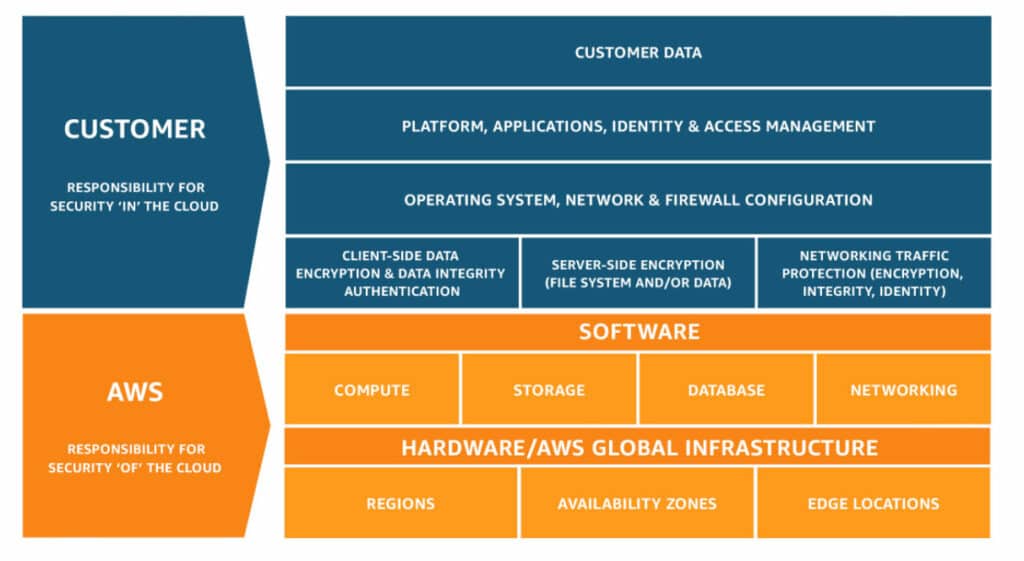
AWS Shared Responsibility Model
Understanding the division of security responsibilities is crucial in AWS environments. We follow the AWS Shared Responsibility Model, ensuring that while AWS takes care of the security ‘of’ the cloud, we focus on security ‘in’ the cloud, covering your responsibilities.
Why is This Service Required? (FUD):
- AWS’s Growing Popularity With AWS’s expansive adoption, ensuring its security becomes paramount.
- Complexity of AWS Configurations The vast array of AWS services can lead to inadvertent misconfigurations.
- Ensuring Benchmark Compliance Regular assessments are crucial for alignment with standards like the CIS Benchmark.
- Dynamic Cloud Threat Landscape Modern threats are evolving, demanding updated and thorough security assessments.
- External Scrutiny Benefits An external review can highlight vulnerabilities and gaps that might be missed internally.

What Will the Customer Gain?
- Holistic AWS Security Overview Comprehensive insights into the current security posture of your AWS environment.
- Strategized Remediation Path Clear, actionable steps to address identified vulnerabilities.
- Guard Against Modern Threats Fortified defenses against AWS-specific and broader cyber threats.
- Resource and Data Assurance Enhanced security measures for critical AWS resources and data.
- Benchmark Compliance Confidence Assurance in alignment with industry benchmarks like the CIS AWS Foundations Benchmark.
What Will Be Assessed?:
- AWS Identity and Access Management (IAM) Detailed assessment of user, group, role configurations, and access controls.
- IAM Access Analyzer Review of access policies to identify potential security risks.
- AWS Config Comprehensive evaluation of resource inventory, configuration history, and compliance measures.
- AWS CloudTrail In-depth analysis of log configurations, data events, and AWS management events.
- AWS CloudWatch Examination of AWS resource monitoring, alarms, and events.
- AWS S3 and EC2 Analysis of AWS Simple Storage Service bucket policies and Elastic Compute Cloud instance configurations.
- AWS VPC (Default) Review of default Virtual Private Cloud settings, emphasizing network security.

Benefits of the Service for Customers
Internal pen tests are a critical cornerstone in fortifying your organization’s cybersecurity defenses from within.
Elevated AWS Security Stance
Achieve a fortified security layer for your AWS environment.
Data Breach Risk Minimization
Reduce potential risks stemming from vulnerabilities and misconfigurations.
Benchmark Alignment
Assurance of alignment with the CIS AWS Foundations Benchmark.
Enhanced Security for
Critical Assets
Leverage Vumetric's in-depth expertise in AWS security.
Comprehensive Assessment
A blend of automated and manual assessment techniques for a complete view.
Clear Security Intelligence
Precise, actionable, and prioritized security guidance.
Got an Upcoming Project? Need Pricing For Your AWS Pentest?
Answer a few questions regarding your cybersecurity needs and objectives to quickly receive a tailored quote. No engagement.
- You can also call us directly: 1-877-805-7475
FAQ
Couldn’t find the information you were looking for? Ask an expert directly.
No, our assessment ensures there are no disruptions, safeguarding the performance and availability of your AWS services.
We advise annual assessments or after major changes to your AWS environment.
The assessment is anchored around the CIS AWS Foundations Benchmark.
Vumetric provides a detailed report presentation, ensuring all questions and clarifications are comprehensively addressed.
Read Our Clients' Success Stories
Discover how our external pentest services helped organization of all kinds improve their network security:
“ Vumetric conducted penetration testing and showed us where we were vulnerable. They made the process smooth, were very responsive and well organized. They really impressed us as specialists in their field. ”
Elizabeth W., General Manager
" Vumetric Cybersecurity was able to complete their tests and provide the client with detailed reports that included issues and remedies. The team was highly proactive and communicative, and internal stakeholders were particularly impressed with Vumetric Cybersecurity's cost-effective approach. ”
Daniel Reichman, Ph.D, CEO and Chief Scientist
“ Vumetric performed manual and automated security testing of our systems. They met our deadlines and kept us updated throughout the testing process. Their presentation of findings and recommendations was engaging and effective. ”
Louis E., Director of IT & CISO
Why Choose Vumetric For AWS Cloud Infrastructure Security Audit?
Vumetric is an ISO9001-certified boutique provider entirely dedicated to pen test, with more than 15 years of experience in the industry. Our methodologies are proven and our understanding of cybersecurity risks is extensive, allowing us to provide clear advice to our clients that is pragmatic, adapted to their needs and efficient in securing against any malicious attacker.
Leading Penetration
testing methodology
Our testing methodologies are based on industry best practices and standards.
ExperiencedTeam
Our team of certified penetration testers conducts more than 400 pentest projects annually.
Actionable Results
We provide quality reports with actionable recommendations to fix identified vulnerabilities.
Download The Vumetric Penetration Testing Buyer's Guide
Learn everything you need to know about penetration testing to conduct successful pentesting projects and make informed decisions in your upcoming cybersecurity assessments.

Featured Cloud Cybersecurity Resources
Gain insight on emerging hacking trends, recommended best practices and tips to improve Cloud security:
Certified Penetration Testing Team
Our experts hold the most widely recognized penetration testing certifications. Partner with the best in the industry to protect your mission critical IT assets against cyber threats.

















