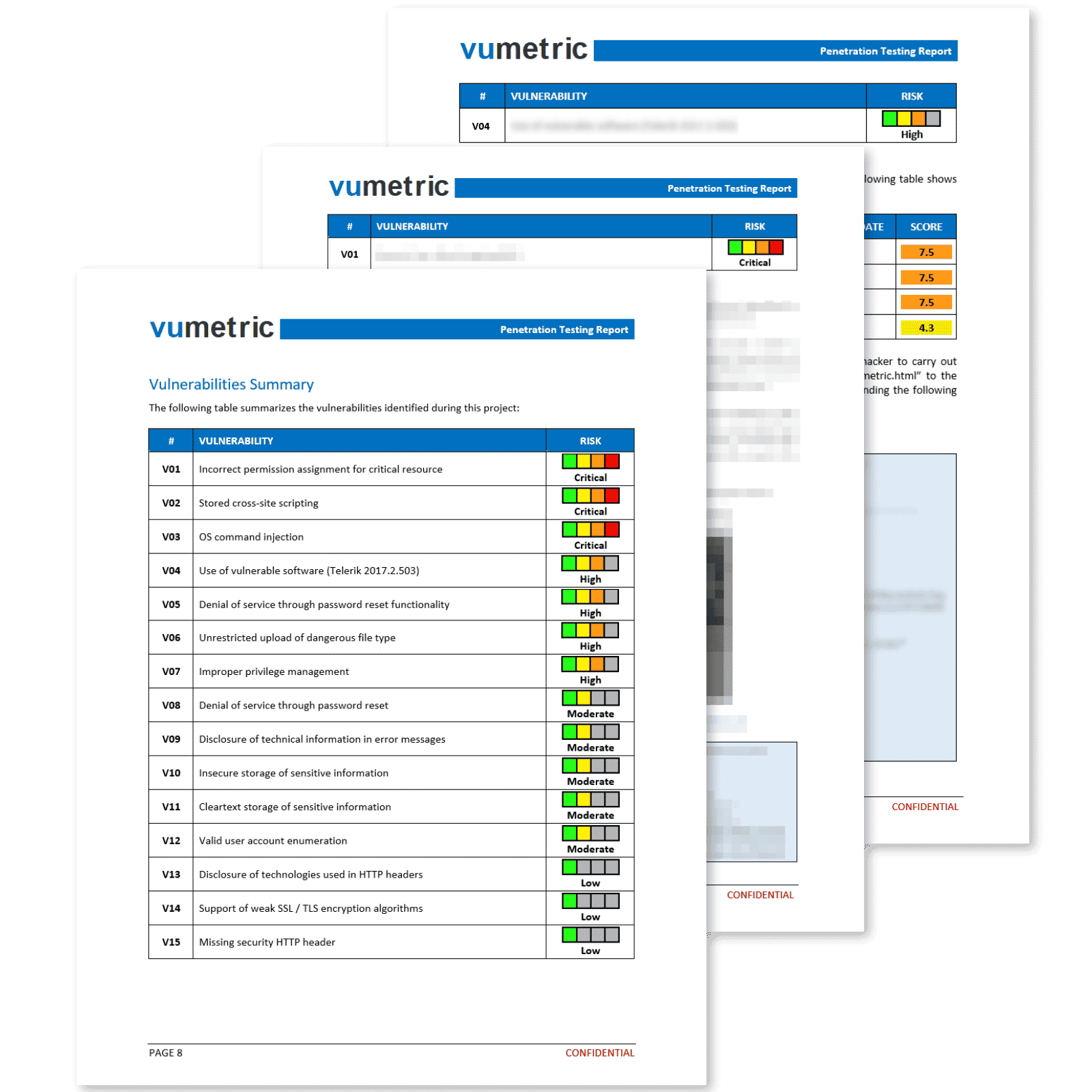
What is IoT Penetration Testing?
Why Conduct a Penetration Test of Your Smart IoT Devices?
By conducting IoT penetration testing, organizations can gain valuable insights into the security posture of their smart devices, whether they are commercial, consumer or industrial products, ensuring the safety and privacy of your end users. Here is what you will get after conducting a project with our team:
Validate your existing security controls
A penetration test will evaluate the effectiveness of your current security measures, helping you understand whether they are adequate to protect your medical devices from potential threats and improving your ability to prevent attacks.
Test the resilience of your devices against targeted attacks
By simulating targeted attacks in a safe and controlled manner, our penetration testing services will ensure that your smart devices can withstand real-world threats and help develop additional measures to prevent potential breaches, giving you confidence that your users are safe.
Understand the potential impact of an attack on your IoT devices
Our team of experts will analyze the potential outcome of a successful breach on your IoT devices for each vulnerability and security risk that could be exploited by hackers in a real-world scenario, enabling you to prioritize remediation efforts and allocate resources efficiently.
Identify & fix all existing vulnerabilities
Our team will identify all existing vulnerabilities and security risks within your smart devices and their underlying infrastructure, allowing you to systematically address these issues, strengthen your overall security posture and reduce your overall risk exposure.
Improve the security of your IoT devices
By uncovering and addressing vulnerabilities, our penetration testing services will help you enhance the security of your IoT products, protecting them from potential breaches that may leak sensitive data or lead to device takeovers.
When Should You Perform an IoT Device Penetration Test?
- Annually as part of a proactive security strategy
- After major changes or updates to the device, mobile application or system
- Before deploying a new system or application to the internet
- As part of regulatory or compliance requirements
- Following a security breach or incident
- In response to a new security threat targeting IoT devices
Our IoT Penetration Testing Services
Our experts have in-depth knowledge of the security risks associated with the use and configuration of IoT devices in a variety of contexts that are specific to each type of device. Our IoT penetration tests include IoT mobile applications, cloud APIs, and communication protocols, as well as integrated systems, and embedded firmware.
Integrated Systems Penetration Testing
Test the security of your integrated systems.
IoT Mobile App
Applications Testing
Test your IoT mobile application's security.
Cloud-Hosted APIs
Penetration Testing
Test the security of your cloud-hosted APIs.
Communication Systems Testing
Test the security of your communication systems.
Common Cybersecurity Risks & Vulnerabilities Identified
Our methodology covers an extensive attack surface, identifying vulnerabilities that are unique to your devices, as well as the most prominent IoT security risks:
Insecure network services & configurations
A security risk where misconfigured network services or insecure protocols expose the IoT devices to potential attacks, allowing unauthorized access, data interception, or disruption of services.
Use of insecure or outdated components
A vulnerability where the use of deprecated, insecure, or outdated hardware or software components within the IoT device exposes it to known vulnerabilities and exploits, increasing the risk of cyber attacks.
Insufficient privacy protection
A security risk where inadequate privacy measures, such as weak data encryption or improper data handling, expose sensitive user information to unauthorized access, potentially leading to data breaches or privacy violations.
Insecure data transfer and storage
Inadequate ecosystem interfaces
A vulnerability where poorly implemented interfaces across the IoT ecosystem, such as web applications, APIs, cloud services, or mobile apps, can be exploited by attackers to gain unauthorized access or compromise the integrity and confidentiality of data.
Lack of secure update mechanisms
A security risk where IoT devices lack proper update mechanisms, leaving them vulnerable to outdated software, unpatched security flaws, or malicious firmware updates introduced by attackers.
OWASP's Internet of Things
- Weak passwords
- Insecure network services
- Insecure ecosystem interfaces
- Lack of secure update mecanism
- Use of insecure components
- Insufficient privacy protection
- Insecure data transfer and storage
- Lack of device management
- Insecure default settings
- Lack of physical hardening
Need Help To Assess And Improve Your Cybersecurity?
Improve Your IoT Device's Security

Healthcare and
medical devices

Smart security systems (locks, cameras, etc.)

Industrial / SCADA
IoT Devices

Electric car
charging station
Frequently Asked Questions
Couldn’t find the information you were looking for? Ask an expert directly.
IoT penetration testing aims to identify and mitigate security vulnerabilities in IoT devices and systems, preventing cyber attacks and ensuring the protection of sensitive data.
The process involves assessing the IoT device’s hardware, firmware, network, wireless communications, mobile and web application interfaces, and cloud APIs. Skilled professionals perform manual testing and analysis to identify known and unknown vulnerabilities.
To begin, you’ll need to provide access to your IoT devices, networks, and any relevant documentation. Our team will discuss your specific requirements and tailor the testing process to your organization’s needs.
Yes, you’ll need to grant our team appropriate access and permissions to your IoT devices, networks, and systems to ensure a thorough and accurate assessment. In most cases, it is not required for you to physically ship the device for us to conduct the test, but in the event that only physical testing can be performed for your specific type of device, all requirements and details will be discussed with your team in a pre-launch team.
Yes, our skilled professionals have experience testing a wide range of IoT devices and systems, including those with custom protocols and proprietary technologies.
IoT penetration testing is an essential part of a comprehensive cybersecurity strategy, more particularly for mission-critical devices and products. It helps identify and remediate vulnerabilities in IoT devices, reducing the risk of cyber attacks and providing a safe and private environment for your users to share sensitive data.
The duration of the test depends on the complexity of the smart device and the scope of the assessment. Typically, it may take anywhere from a few days to 3 weeks to complete.