What is ICS / SCADA Penetration Testing?
ICS / SCADA penetration testing is a type of assessment designed to identify and fix vulnerabilities in industrial systems or devices that could be exploited by an attacker by simulating the same techniques used by hackers. These control systems represent the nervous system of today’s supply chain and their increasing complexity comes with a new set of cybersecurity risks. Our services allow you to determine how your industrial networks and devices could be hacked, providing actionable and tailored recommendations to secure your installations from cyberattacks.
Why Conduct a SCADA Pentest?
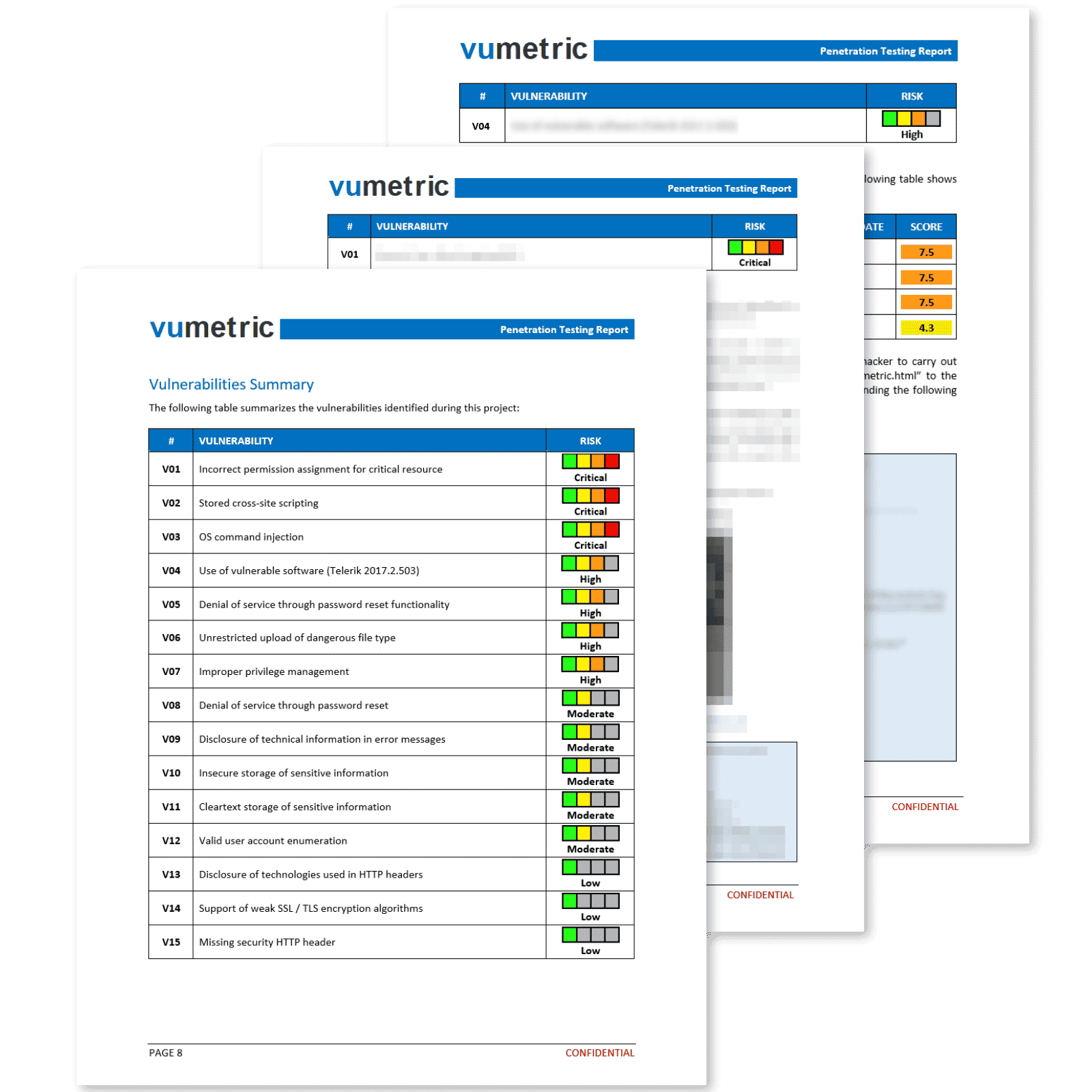
Conducting a penetration test of your SCADA provides invaluable insights into the potential cyber threats that may compromise your automated processes. Here is what you will get after conducting a project with our team:
Validate your existing security controls
A penetration test will evaluate the effectiveness of your current security measures, helping you understand whether they are adequate to protect your SCADA systems from potential threats and improving your ability to prevent attacks.
Test the resilience of your systems against targeted attacks
By simulating targeted attacks in a safe and controlled manner, our penetration testing services will ensure that your SCADA systems can withstand real-world threats and help develop additional measures to prevent potential disruptions to your automations, giving you confidence in their security.
Understand the potential impact of an attack on your SCADA / ICS devices and networks
Our team of experts will analyze the potential outcome of a successful breach on your SCADA systems for each vulnerability and security risk that could be exploited by hackers in a real-world scenario, enabling you to prioritize remediation efforts and allocate resources efficiently.
Identify & fix all existing vulnerabilities
Our team will identify all existing vulnerabilities and security risks within your SCADA systems, allowing you to systematically address these issues, strengthen your overall security posture and reduce your overall risk exposure.
Enhance the security of your critical infrastructure and processes
By uncovering and addressing vulnerabilities, our penetration testing services will help you enhance the security of your critical infrastructure and automated processes, protecting your organization from potential disruptions incurring significant financial losses.
When Should You Perform a SCADA Penetration Test?
Organizations should regularly conduct SCADA penetration testing to ensure their systems remain secure. Factors to consider when determining the frequency and timing of these tests include:
- Annually, as part of a proactive security strategy
- After significant changes to the SCADA environment
- When adding new, sensitive features or components
- Following a security incident or breach
- As part of a regulatory or compliance audit
- In response to new vulnerabilities identified in technologies used
- In response to new threats targeting automated processes
Our ICS / SCADA Penetration Testing Services
SCADA
Penetration Testing
Test your SCADA's security.
IT / OT
Penetration Testing
Test the security of your IT / OT.
Industrial Control System
Cybersecurity Assessment
Assess the security of your ICS systems.
Firewall
Security Audit
Assess your firewall configurations.
Network Segmentation
Security Audit
Assess your network segmentation.
Industrial Control System
Security Roadmap
Get a prioritized cybersecurity roadmap.
Common Cybersecurity Risks & Vulnerabilities Identified
Weak access controls & authentication
A security risk where attackers can exploit inadequate access controls or weak authentication methods to gain unauthorized access to SCADA systems, potentially manipulating processes or stealing sensitive data.
Insecure SCADA protocols & app vulnerabilities
Security flaws in SCADA protocols or applications can be exploited by attackers to gain unauthorized access, disrupt processes, or steal sensitive information.
Inadequate encryption & communication
Weak encryption methods or insecure communication channels can be exploited by attackers to intercept sensitive data, manipulate processes, or compromise the confidentiality and integrity of the SCADA system.
Insecure network configurations & segregation
A risk where improper network configurations or insufficient network segregation allows attackers to infiltrate the SCADA system, compromising its security and potentially disrupting critical processes.
Administrator privileges escalation
Attackers can exploit vulnerabilities to elevate their privileges, gaining administrator-level access to SCADA systems, allowing them to manipulate processes, exfiltrate data, or install malicious software.
Misconfigurations & unpatched vulnerabilities
Poorly configured systems, default settings or unpatched versions with vulnerabilities can leave SCADA systems vulnerable to unauthorized access, allowing attackers to exploit weaknesses and compromise the security of the system.
Securing ICS Against Digital Threats
Our specialists offer complete SCADA penetration testing solutions that can be performed on environments in production without impacting your normal operations. Our approach will enable your organization answer the following:
Are your SCADA systems accessible from the IT network?
Have you evaluated the security of your control network?
Can your network be hijacked and used by malicious actors?
Have you fixed common vulnerabilities present in SCADA systems?
Have you assessed the potential impact of lost production and damaged equipment if the control network is attacked?
Improve Your SCADA Security

Oil and
Gas

Manufacturing and processing

Water treatement and distribution

Smart
transport

Smart
buildings

Energy generation ad distribution

Heavy
industry

Food
production
Common Industrial Cybersecurity Risks
40%
are connected to the public internet
57%
of sites do not automatically update anti-virus signatures
84%
have at least one remotely accessible device
53%
have outdated operating systems (such as Windows XP)
69%
have plain-text passwords traversing their ICS networks
22%
are being actively exploited by hackers
Need to Conduct a Penetration Test of Your ICS/SCADA?
Vumetric, Leader in SCADA Penetration Testing
Manual testing based on real-world attack methods
Detailed ICS / SCADA reporting - Technical and executive
Prioritized vulnerabilities with step-by-step corrective measures
In-production testing with limited impact
Evidence of identified risks
Frequently Asked Questions
Couldn’t find the information you were looking for? Ask an expert directly.
The purpose of SCADA penetration testing is to identify vulnerabilities and security risks in Supervisory Control and Data Acquisition (SCADA) systems, which are critical for monitoring and controlling industrial processes and infrastructure. It ultimately provides remediation measures and improvements to mitigate any potential cyber threats.
The process involves customized testing methods, including reconnaissance, port scanning, identifying weak access controls, network equipment security controls testing, administrator privileges escalation testing, password strength testing, network segregation, exploitation research, brute force attacks, denial of service checks, and manual vulnerability/configuration weakness testing and verification.
To get started, you need to provide information about your SCADA environment, network topology, and access to the systems for testing. Additionally, a clear scope and objectives for the test should be defined.
Our SCADA penetration testing services are designed to test live systems without causing any interruptions to your usual operations. We take several precautions to make our tests unnoticeable, minimizing disruptions. Our team is experienced in working with live environments and will establish a point of contact for escalating critical findings or addressing potential impact on productivity, ensuring a smooth and secure testing process.
Yes, you will need to grant access and permissions to the testing team, allowing them to perform the necessary tests and assessments on your SCADA systems remotely. Our experts will offer various solutions to remotely access your SCADA systems in an efficient and secure manner. All access and documentation requirements will be discussed with your team in a pre-launch call.
SCADA penetration testing is a crucial part of a comprehensive cybersecurity strategy for any company relying on these automated systems for their daily operations. This test focuses on the specific risks and vulnerabilities of SCADA systems, which are often overlooked in traditional security assessments.