What is a Purple Team Exercice?
Purple team exercises are assessments designed to measure an organization’s IT systems and employees’ ability to respond to a generalized cyberattack, by simulating both the offensive (red team) and the defensive team (blue team) in order to determine which attacks were successfully blocked and which would have lead to a cyber incident. It is particularly useful at preventing cyberattacks, as it gives direct insight into how the organization performs in a real-world hacking scenario and provides a better overview of the necessary measures to implement in order to prevent incidents.
Red Team vs Purple Team vs Blue Team

Red Team
- Penetration testing
- Social engineering
- Automated scanning
- Vulnerability exploitation

Purple Team
- Offensive and defensive
- Threat detection
- Collaborative security
- Security improvements

Blue Team
- Defensive security
- Gap analysis
- Forensics & threat hunting
- Incident response & SOC
Why Conduct Purple Teaming?
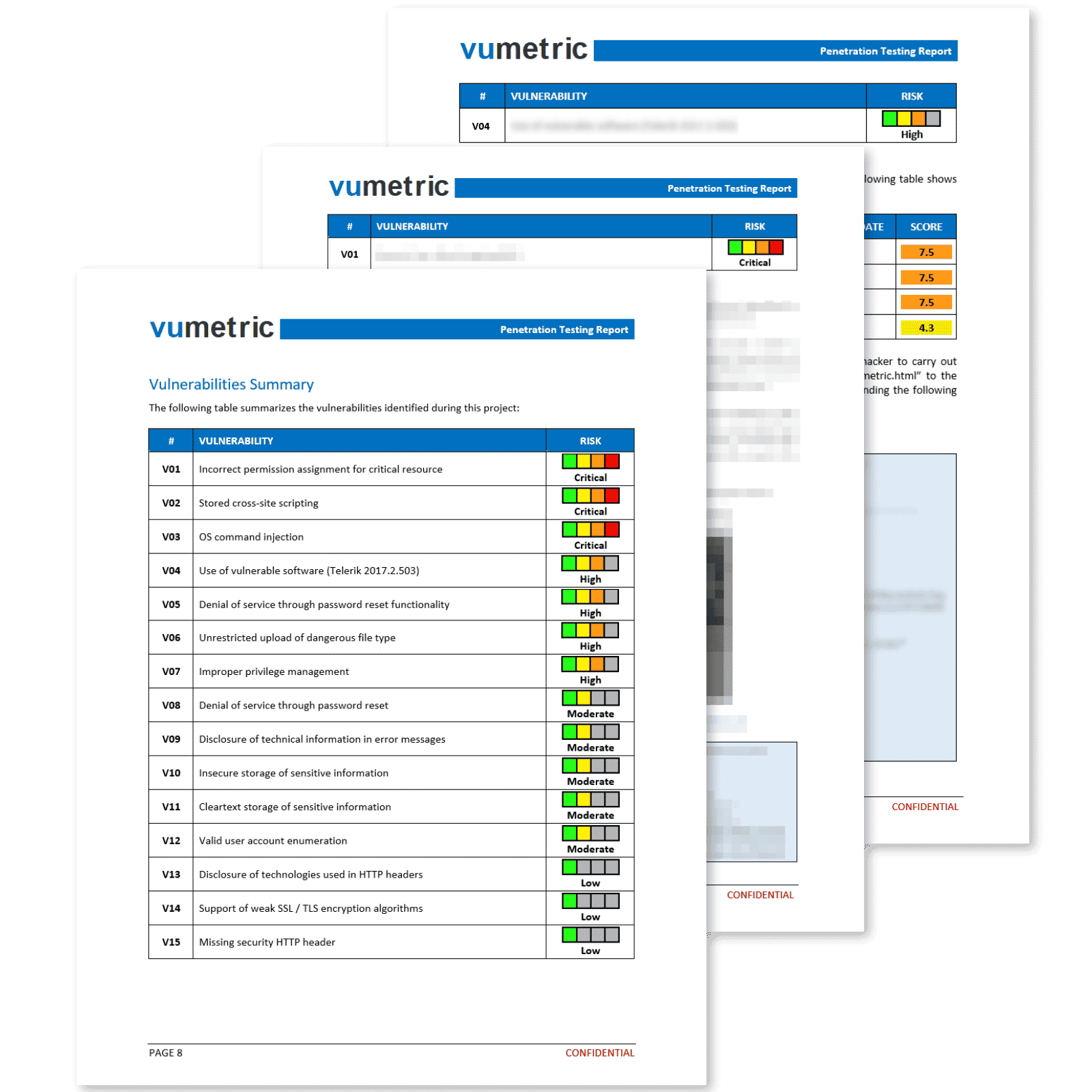
A purple team assessment is a comprehensive security evaluation that simulates a real-world cyberattack in order to test an organization’s defenses. It helps organizations identify weaknesses in their security posture and make improvements before they are exploited by attackers. The assessment can also help organizations to better understand their adversaries and how they operate, which can aid in the development of more effective security countermeasures.
It combines the benefits of red & blue teaming in order to paint a more accurate picture of your cybersecurity risks that should be prioritized.
Gain a better understanding of how hackers operate and how to block them
Effectively benchmark your resilience to true and tried hacking techniques
Improve your internal security team's comprehension of your cybersecurity
Streamline future security investments by identifying most prominent risks
Get critical insight into the cost/benefit of various security measures
DID YOU KNOW?
“ The demand for cybersecurity specialists able to conduct purple teaming assessments has increased by 70% since 2020 ”
Need Help To Assess And Improve Your Cybersecurity?
Protect Your Organization From Persistent Hackers