What is Thick Client Penetration Testing?
Thick client penetration testing is an assessment designed to identify and fix cybersecurity vulnerabilities in desktop applications using the same tools and techniques as hackers. Whether the thick client built on a two tier or three tier architecture, our assessments allow organizations to identify and fix real-world opportunites for hackers to exploit their company’s applications to launch further malicious acts on their user’s computer.
Why Conduct a Thick Client Pentest?
Validate your existing security controls
Our tests will test the effectiveness of your app’s existing security controls in preventing and detecting attacks. By simulating an attacker, our experts will identify gaps in your defenses and provide remediation measures to improve your ability to prevent cyberattacks.
Understand the potential impact of an attack on your thick client
Our tests will identify and measure vulnerabilities that could be exploited to gain unauthorized access to sensitive data or launch further attacks on your user’s computer. By understanding exactly what could happen during an attack, organizations can prioritize their security efforts and allocate resources effectively in securing mission-critical applications.
Identify & fix all existing vulnerabilities
Our team will help you identify all existing vulnerabilities in your mobile application and its underlying hosting infrastructure, whether it’s cloud-based or in-house. The test will result in prioritized remediation steps to help reduce your overall risk exposure.
Improve your thick client's security
Our services will provide detailed information on how an attacker can breach your thick client, what data or critical systems they could target and how to protect them. With this information, our team will provide you with tailored recommendations to improve your application’s security posture and protect it against potential threats.
Enhance your development practices
Gain a deeper understanding of development processes that might inadvertently introduce security risks, allowing you to develop more secure applications and features in the future.
When Should You Perform a Penetration Test of Your Thick Client?
- Annually as part of a proactive security strategy
- Before launching new sensitive features or a major update
- After significant infrastructure or code changes
- Prior to a compliance audit or assessment
- Following a security breach or incident
- In response to newly discovered vulnerability or threats
- Prior to an M&A transaction or other major business event
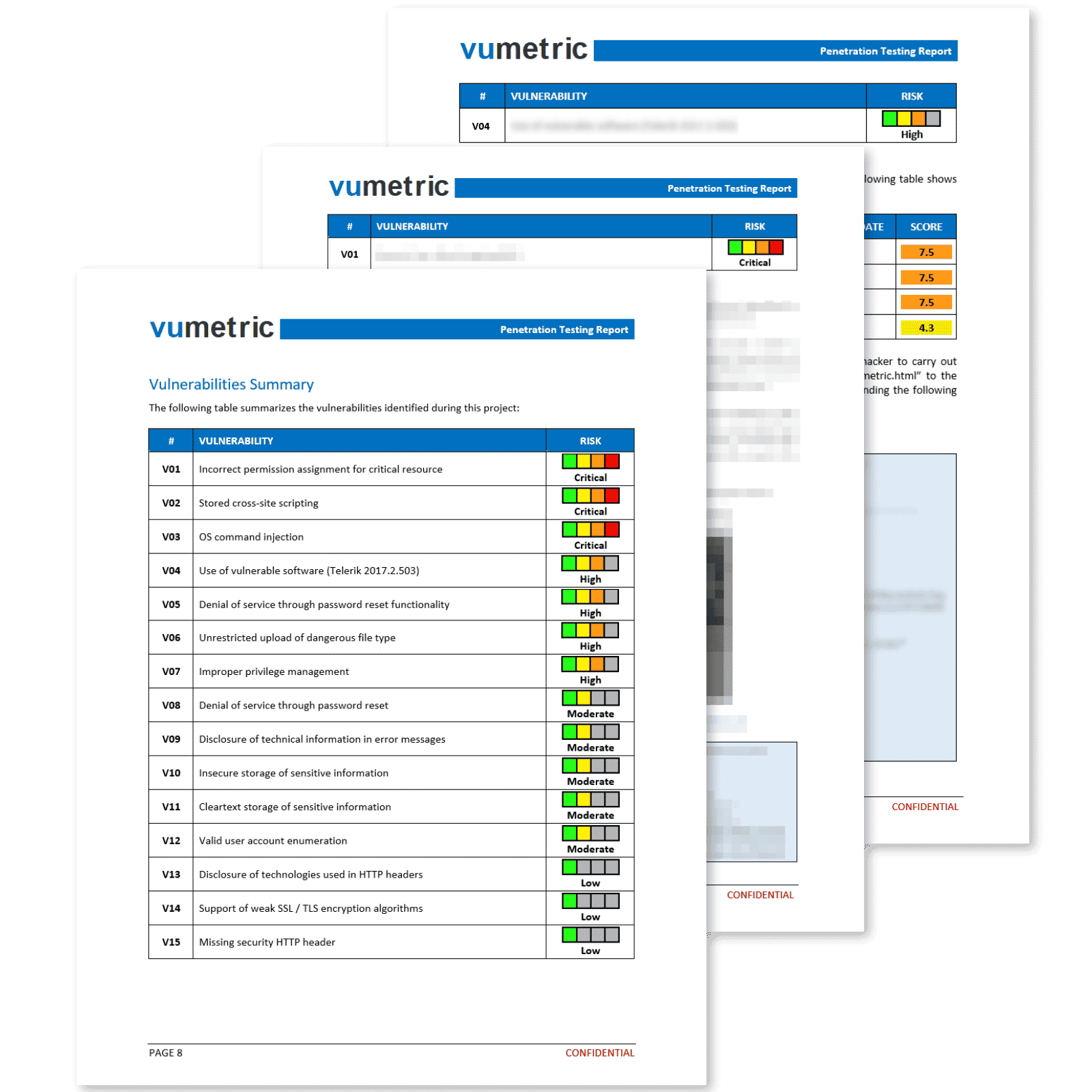
Common Cybersecurity Risks & Vulnerabilities Identified
Thick clients often store a lot of sensitive data locally, making it a prime target for attackers looking to steal sensitive information.
Our thick client penetration testing services identify risks unique to your application and cover the most common vulnerabilities and identify risks unique to your application with the help of manual techniques.
Hardcoded data & authentication tokens
A security issue where sensitive information, such as passwords or API keys, is embedded directly into the application’s source code, making it easier for attackers to discover and exploit these credentials to gain unauthorized access.
Vulnerable network protocols & communications
A security risk where insecure or misconfigured network protocols are used, enabling attackers to intercept, tamper with, or inject malicious data into the communication between the client and server, leading to data breaches or system compromise.
Business logic flaw
A security issue where the application’s core functional processes are not properly validated or enforced, potentially allowing attackers to manipulate the application’s intended behavior and exploit it to gain unauthorized access or perform malicious actions.
Improper handling of user permissions & roles
A vulnerability where an application fails to properly manage and enforce user access rights, potentially allowing unauthorized users to perform actions or access sensitive data beyond their intended permissions.
Weak or broken authentication & sessions:
A vulnerability where an application does not implement robust mechanisms for verifying user identities and maintaining secure user sessions, making it easier for attackers to impersonate legitimate users or hijack user sessions to gain unauthorized access.
Memory corruption vulnerabilities
A security risk where programming errors or inadequate memory management can lead to unpredictable application behavior, potentially allowing attackers to execute arbitrary code, crash the application, or gain unauthorized access to system resources.
Why Choose Vumetric For Your Thick Client Penetration Test?
Our thick client penetration testing services have helped hundreds of organizations fix vulnerabilities in their mission-critical applications.
Real-world expertise - Our consultants have tested and successfully secured thick clients of all types, from security software to utility tools.
Manual testing - Our tests combine manual techniques and automated tools in order to identify vulnerabilities unique to your thick client.
Flexibility - Each project is tailored to your context and needs to maximize the results. We don't believe in a cookie-cutter approach.
Consultant approach - To guarantee a successful project, we present our findings and recommendations to your stakeholders to ensure full comprehension of the identified risks and proposed corrective measures.
Need Help To Assess And Improve Your Cybersecurity?
Frequently Asked Questions
Couldn’t find the information you were looking for? Ask an expert directly.
The purpose of a thick client penetration test is to identify and address cybersecurity vulnerabilities in your organization’s proprietary desktop applications, ensuring the security of sensitive data, preventing unauthorized access by attackers and protecting your end user.
The process includes application scoping, mapping and service identification, reconnaissance and enumeration, application scanning, vulnerability identification, post-exploitation, strategic mitigation, and patch verification. A combination of automated tools and manual techniques is used to identify vulnerabilities and propose appropriate solutions.
To prepare for a thick client penetration test, you should gather documentation on the application’s architecture, provide access to the testing environment (if available), and designate a point of contact for communication with our testing team.
In most cases, no specific access is required for the test, as the goal is to replicate a real-world attack scenario. However, depending on the features available on the thick client or the specific goals of the test, some level of access or permissions may be necessary. This will be determined in collaboration with our team, ensuring that the test is tailored to your application and security objectives while maintaining a realistic approach.
The duration of a thick client penetration test depends on the complexity and size of the application. On average, tests can take anywhere from a few days to a few weeks.
Thick client penetration testing is an essential component of your overall application security strategy, more particularly for mission-critical apps, as it helps you identify & fix vulnerabilities to ensure your end users have a secure environment to share sensitive data and conduct their daily operations.
Vumetric can test a wide variety of thick clients, ranging from enterprise software and financial applications to utility tools and multimedia applications. Our team of experts has experience in testing thick clients built on various technologies, architectures, and platforms, ensuring a comprehensive assessment of your desktop application’s security, regardless of its complexity or industry-specific requirements.