Vumetric, Your Trusted
Penetration Testing Provider
Penetration testing has become one of the most critical step in a cybersecurity risk managment strategy and is now conducted by the wide majority of organizations, but given the technical nature of the subject, it comes with many misconceptions or misunderstandings.
Leverage our 15 years of experience in conducting pentesting to determine what type of cybersecurity assessment your organization needs, ensure it is aligned with your business objectives and get tips to pick a provider.
Penetration Testing Guide
(2024 Edition)
Everything you need to know to scope, plan and execute successful pentest projects aligned with your risk management strategies and business objectives.
- The different types of penetration tests and how they compare
- The use cases of vulnerability scans VS. pentests
- The industry's average cost for a typical project
- What to expect from a professional report
- 20 key questions to ask your prospective provider
Get In Touch With Our Team
- Identify vulnerabilities beyond the capabilities of an automated test
- Get detailed step-by-step recommendations on how to fix them
- Achieve compliance with standards (SOC 2, PCI-DSS, ISO 27001, etc.)
- Inform management on risks and remediations
- Gain full confidence in your cybersecurity
Contact a Vumetric expert to further discuss how we can help.
External Penetration Testing
Case Study
See our industry-leading services in action and discover how they can help secure your external network perimeter from modern cyber threats and exploits.
- Project findings of a real external pentest project
- List of identified vulnerabilities prioritized by risk level
- Attack path overview and steps
- Outcome of the project
- And more
Web Application Penetration Testing
Case Study
See our industry-leading services in action and discover how they can help secure your mission-critical Web Apps / APIs from modern cyber threats and exploits.
- Project findings of a real external pentest project
- List of identified vulnerabilities prioritized by risk level
- Attack path overview and steps
- Outcome of the project
- And more
Internal Penetration Testing
Case Study
See our industry-leading services in action and discover how they can help secure your internal network infrastructure from modern cyber threats and unauthorized access.
- Project findings of a real internal pentest project
- List of identified vulnerabilities prioritized by risk level
- Attack path overview and steps
- Outcome of the project
- And more
What's a Penetration Test?
Penetration testing is a security assessment that simulating real-world attacks used by hackers to identify vulnerabilities in a business’s IT systems, networks, applications, medical devices, etc. It’s crucial for enhancing security by exposing weaknesses before attackers can exploit them. This proactive measure helps businesses strengthen their defenses, safeguard sensitive data, comply with regulatory requirements, and improve their resilience against the latest security threats their organizations is most vulnerable to.
Given the growing complexity of cyber risks, pentesting has become a critical tool for IT leaders and company stakeholders to determine where they are most at risk of being breached so they can prioritize and allocate their improvement efforts as efficiently as possible.
Outsourcing Pentesting to a Provider vs. Conducting In-House
While it’s entirely possible for IT departments to conduct pentesting internally, this skillset is not common and rarely possessed by IT professionals. Working with an external company simplifies the process for your IT team, providing an independent audit of security practices to help hold teams accountable. The practical recommendations help focus resources on implementing fixes that significantly improve resilience against prevalent hacking threats.
Efficiency
Providers have refined processes to deliver comprehensive, reliable results faster and at lower cost than internal teams.
Testing Expertise
Testers have a highly specialized skillset acquired through conducting hundreds of diverse projects annually.
Unbiased Perspective
Providers provide an objective, independent review of the security posture without internal politics or conflicts of interest.
Continuous Training
Pentest specialists stay up to date with the latest threats and hacking techniques through continuous certifications and training.
Accountability
Outsourcing your assessment helps hold internal teams or IT providers accountable by benchmarking against an independent audit.
Compliance
Penetration testing providers will provide documentation that helps demonstrate compliance with standards efficiently.
Network Penetration Testing
External network penetration testing
This test focuses on identifying vulnerabilities from an outsider’s perspective, ensuring IT infrastructures and applications are guarded against evolving external threats and hacking methods.
Internal network penetration testing
It aims to uncover vulnerabilities within the organization’s network that automated tools might miss, simulating potential insider attacks or breaches that have surpassed external defenses.
Wireless network penetration testing
With increasing compliance standards, this testing assesses wireless network security against unauthorized access, ensuring these networks do not become gateways for cyber threats.
Mainframe penetration testing
Targets the security of mainframe systems, identifying gaps that standard security measures like firewalls and antivirus might not cover, ensuring comprehensive protection.
Industrial SCADA penetration testing
Specialized testing for Industrial Control and SCADA systems, focusing on vulnerabilities unique to networks and devices controlling physical processes, crucial for maintaining operational integrity in industrial sectors.


Application Penetration Testing Services
Web application penetration testing
This test offers deep dives into the security of web applications using manual attack techniques to reveal complex vulnerabilities, offering a detailed security assessment beyond what automated scans can detect.
Mobile application penetration testing
Simulates hacking techniques to uncover vulnerabilities in mobile apps, focusing on areas like unauthorized access and software exploitation, identifying key security weaknesses.
API penetration testing
Assesses APIs against recognized security standards to determine their external security posture, helping gauge their resilience to common vulnerabilities.
Thick client penetration testing
Targets proprietary desktop applications with advanced security measures to mitigate a broad spectrum of threats, aiming to minimize potential attack vectors.
Source code review
A meticulous examination of an application’s source code to spot security flaws early, integral for reinforcing security from the initial development stages.
Smart Device Penetration Testing
Identifies vulnerabilities and security risks in smart devices and their underlying infrastructure from commercial, industrial and consumer IoT devices to medical equipment used in patient care and analysis.
Medical Device Penetration Testing
Identifies vulnerabilities in medical devices responsible for patient care or medical analysis like IV pumps and imaging systems. This assessment is key in ensuring safety, privacy and meeting FDA cybersecurity compliance requirements.
IoT / Smart Device Penetration Testing
Identifies risks unique to connected devices, covering hardware, network communication, firmware, interfaces & protocols for devices ranging from smart home tech, security systems, to logistics fleet management, industrial supply lines and more.


Adversary Simulation / Red Team
Red Team Assessment
Replicates a skilled and persistent attacker attempting to breach your cybersecurity by any means necessary, across all technologies used by the organization, challenging the effectiveness of employees and systems to detect and respond to a real-world cyberattack.
Purple Team Assessment
Measures an organization’s IT systems and employees’ ability to respond to a generalized cyberattack, by simulating both the offensive (red team) and the defensive team (blue team) in order to determine which attacks were successfully blocked and which would have lead to an incident.
Phishing Simulation Test
Conducts targeted phishing campaigns to test employee awareness and response, serving as a practical measure of the organization’s security awareness training effectiveness.
Cloud Penetration Testing Services
Evaluates security in cloud-hosted assets across major platforms like AWS, Azure, and Google Cloud, considering unique cloud configurations.
Amazon Web Services (AWS) Penetration Testing
Analyzes AWS environments, including network configurations, firewalls, IDS/IPS, and VPNs, to identify and mitigate potential security issues.
Microsoft Azure Penetration Testing
Assesses Azure-hosted web and mobile applications and APIs against common vulnerabilities like the OWASP top 10 and business logic flaws.
Microsoft Office 365 Security Audit
Reviews security across cloud platforms (AWS, Azure, Google Cloud), examining specific components and configurations for vulnerabilities.
Google Cloud Platform Penetration Testing
Tests the security of devices and applications within Google Cloud, covering medical devices, consumer products, and IoT devices, focusing on their features and protocols.
Top Pentest Methodologies & Standards
We leverage the latest testing methodologies and standards to help protect organizations against the latest security threats and hacking techniques used by hackers to breach your cybersecurity.
- OWASP for Application Security
- MITRE ATT&CK Framework
- OSSTMM Open Source Security Testing Methodology
- PTES Penetration Testing Execution Standard
Why Organizations Trust Vumetric For Penetration Testing
Vumetric is a boutique company entirely dedicated to providing comprehensive penetration testing and specialized cybersecurity services. We pride ourselves on delivering consistent and high-quality services, backed by our ISO 9001 certified processes and industry standards. Our world-class cybersecurity assessment services have earned the trust of clients of all sizes, including Fortune 1000 companies, SMBs, and government organizations.
Recognized Expertise
Certified Professionals
Proven Methodologies
Independance & Impartiality
Reputation & Trust
No Outsourcing
Certified Team of Security Experts
Partner with the best in the industry to protect your mission critical IT assets against cyber threats.














Industry Leaders Count on Vumetric to Improve Their Cybersecurity
“ They had friendly staff and realistic down-to-earth recommendations ”
Mark D, IT Director
Mid-Market
“ I'm impressed by the common sense and technical skills of the team. ”
Carl P, Director of Infrastructure & Security
Mid-Market
“ The team is extremely knowledgeable in what they do ”
Wes S, IT Manager
Enterprise
“ Amazing team of experienced cybersecurity professionals! ”
VP, Research and Development
Mid-Market
Explore the latest customer reviews for Vumetric’s penetration testing and cybersecurity solutions to dive deeper into how we help organizations of all types.




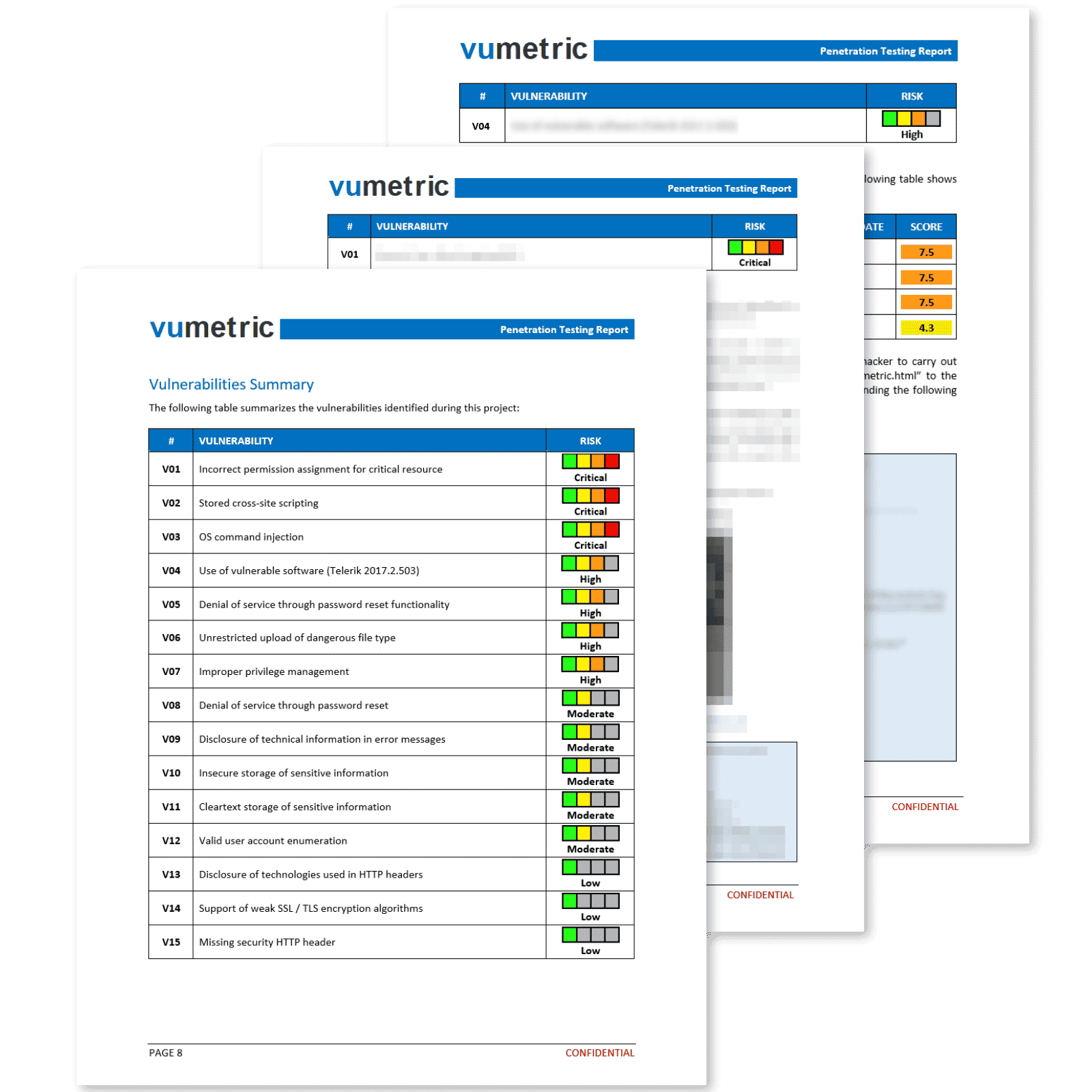
Professional Reporting With Clear & Actionable Results
Our penetration reports deliver more than a simple export from a security tool. Each vulnerability is exploited, measured and documented by an experienced specialist to ensure you fully understand its business impact.
Each element of the report provides concise and relevant information that contributes significantly towards improving your security posture and meeting compliance requirements:
Executive Summary
High level overview of your security posture, recommendations and risk management implications in a clear non-technical language.
Suited for non-technical stakeholders.
Vulnerabilities & Recommendations
Vulnerabilities prioritized by risk level, including technical evidence (screenshots,
requests, etc.) & recommendations to fix each vulnerability.
Suited for your technical team.
Attestation
This document will allow you to meet compliance and regulatory reporting requirements efficiently and with minimal overhead.
Suited for third-parties (clients, auditors, etc).
Our Penetration Testing Process
Here’s a high-level overview of each stage in our proven penetration testing process. We keep you informed at every step of the project.
Project Scoping
Duration: ~ 1-2 days
Activities: We learn about your specific needs and objectives.
Outcome: Business proposal, signed contract.
Kick-off / Planning
Duration: ~ 1 hour
Activities: We review the scope of work, discuss requirements and planning.
Outcome: Scope validation, test planning.
Penetration Testing
Duration: ~ 2-3 weeks
Activities: We execute the test in accordance with the project scope.
Outcome: Detailed penetration test report, presentation.
Remediation Testing
Duration: Up to 1 month
Activities: We test and validate vulnerability fixes.
Outcome: Remediation report, attestation.
Vumetric PTaaS Platform
Vumetric’s Penetration Testing as-a-Service (PTaaS) platform is designed for organizations looking for a modern solution to manage their cybersecurity assessments.
- Request new cybersecurity projects on-demand
- View & compare previous results all in one place
- Track the real-time progress of your assessments
- Invite your team members & manage their permissions
- Available on AWS & Azure Marketplaces
The Limitations of Automated Testing
Limited scope
Automated testing can only detect known vulnerabilities in a predefined set of systems and applications. In contrast, manual penetration testing can adapt to different environments and identify vulnerabilities in proprietary applications with unique configurations.
Lack of context
Automated tools do not understand the context of an organization’s environment or the potential impact of a vulnerability. Expert-driven penetration testing provides a better understanding of the risks, prioritizing them based on the organization’s specific needs.
Limited modern exploits
Automated tools may struggle to keep up with the latest attack techniques used by cybercriminals, as they rely on predefined exploits. Manual pentesting leverages human ingenuity and creativity, as well as knowledge of the current threat landscape to identify & exploit vulnerabilities that automated tools consistently miss.
Limited capabilities
Automated tools can have difficulty exploiting complex vulnerabilities that require a multi-step process or chaining of different weaknesses. Expert-driven penetration testing can uncover these sophisticated attack paths that lead to significant breaches.
Limited remediation guidance
Automated tools often provide generic remediation advice that may not be applicable to a specific organization’s environment. Manual penetration testing offers tailored recommendations, considering the unique context of the risk in the organization.
False positives / negatives
Automated tools may generate false positives, flagging issues that are not actual vulnerabilities, or false negatives, missing real security risks. Expert-driven penetration testing validates findings to ensure you focus remediation efforts on the right priorities.

Real-Life Example of a Hacker's Attack Path

FAQ About Penetration Testing
Couldn’t find the information you were looking for? Ask an expert directly.
What is the purpose of conducting a penetration test?
The process involves an initial pre-engagement phase to define scope and objectives, followed by reconnaissance, scanning, exploitation, and post-exploitation stages to identify vulnerabilities and assess potential impacts. Detailed reports are provided after testing to help you understand and address discovered issues.
How is it conducted? What is the process?
Web application pen test should ideally be performed at least annually to ensure consistent security against evolving threats. Additionally, it’s recommended to conduct a pen test after any significant changes or updates to the application or its hosting infrastructure, as new features, integrations or modifications can introduce new unknown vulnerabilities.
How much does it cost?
The cost of a penetration test varies significantly according to a number of factors. The most determining factor is the size (such as the number of the IP addresses being targeted) and the complexity of the testing scope (the number of features in an application, for instance).
Learn more about the main factors that determine the cost of a penetration test →
Quickly receive a free quote with no engagement using our streamlined quoting tool →
Can penetration testing cause disruptions or downtimes?
Our penetration tests are designed to minimize disruption to your organization’s normal operations and the overwhelming majority of our tests are unnoticeable to our clients. Our team will work with you prior to the project launch to determine any areas that may be susceptible to affect your productivity and will take the necessary steps to minimize any potential impact.
Do we need to provide any access or permissions for the test to be conducted?
In most cases, no access or permissions are required for a penetration test. The goal is to replicate an authentic cyber threat attempting to circumvent your security measures therefore the test is conducted entirely without any inside knowledge or access. However, some types of tests may require access is required to achieve the desired outcome. For example, in order to accurately test an industrial system, remote access to the network may be needed. We will coordinate with your team during the project launch call, where we will confirm objectives, the testing target, as well as any access requirements to achieve project goals.
Will the test allow us to meet compliance requirements?
Our penetration tests helps several organizations of all types meet compliance requirements every year by identifying vulnerabilities that need remediation. Once remediation testing is completed, we provide an official attestation confirming that vulnerabilities have been remediated, helping organizations meet compliance requirements efficiently without requiring them to share confidential and sensitive information regarding their cybersecurity risks to a third-party.
How long does it take?
The duration of the test varies depending on the size and complexity of the scope. A typical pentest project can range from a few days, up to 3 weeks.
BUILD A QUOTE
RECEIVE YOUR QUOTE QUICKLY
What you will get in your detailed quote:
Activities
Including methodologies
Deliverables
Report table of content
Total cost
All-inclusive flat fee
More than 500 organizations received a quote from us in 2023
BOOK A MEETING
Schedule a Meeting With The Team
Looking for more details on how we can help or need guidance to determine the approach best suited for your organization? Plan a virtual meeting with a member of our team to discuss further without any engagement.
* No free email provider (e.g: gmail.com, hotmail.com, etc.)
What happens next?
A Vumetric expert learns about your needs and objectives during a quick meeting.
A project scope is defined (target environment, deadlines, requirements, etc.)
A detailed quote including all-inclusive pricing and statement of work is provided.







